40 aws best practices
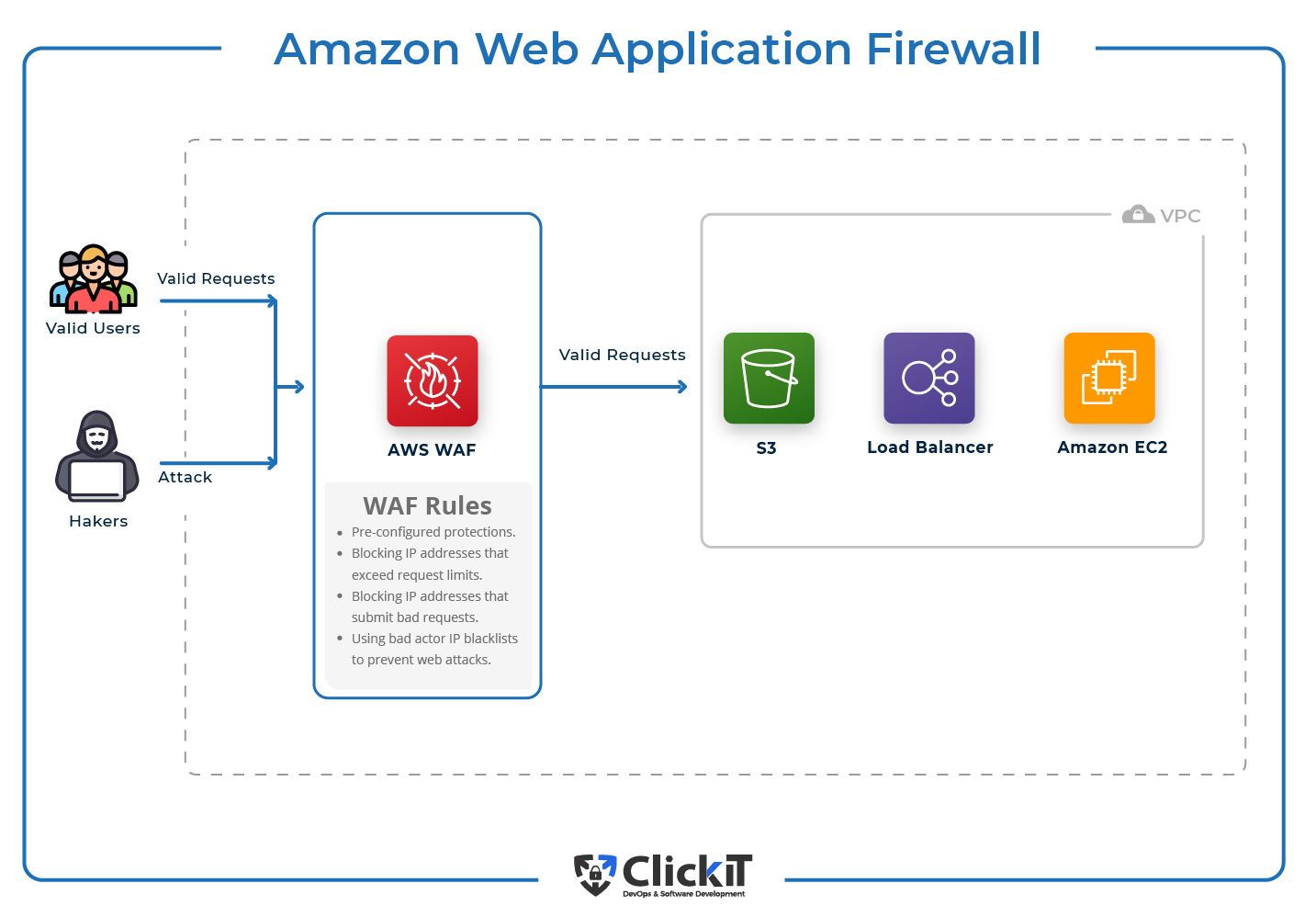
21 AWS Security Groups Best Practices | McAfee Blog As with any AWS service, it is crucial that AWS security groups are properly configured to protect against security risks and threats and best practices are followed: 1) VPC flow logging: Enable Virtual Private Cloud (VPC) flow logging. VPC flow logs provide visibility into network traffic that traverses the VPC and can be used to detect ... 13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
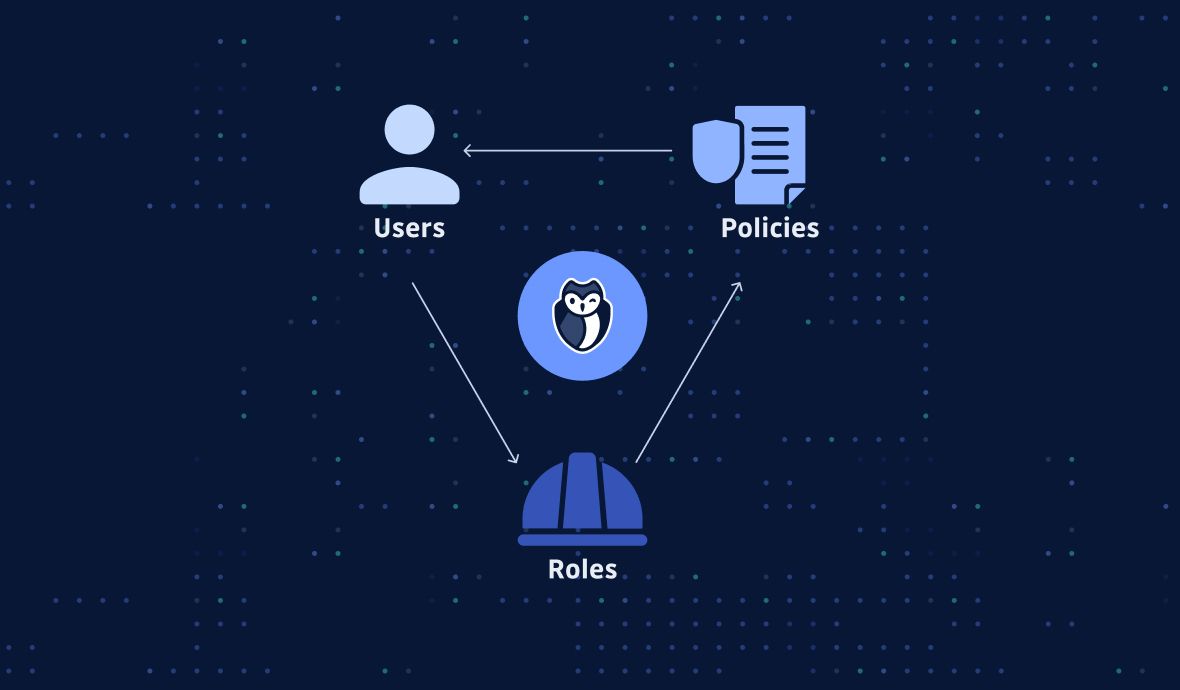
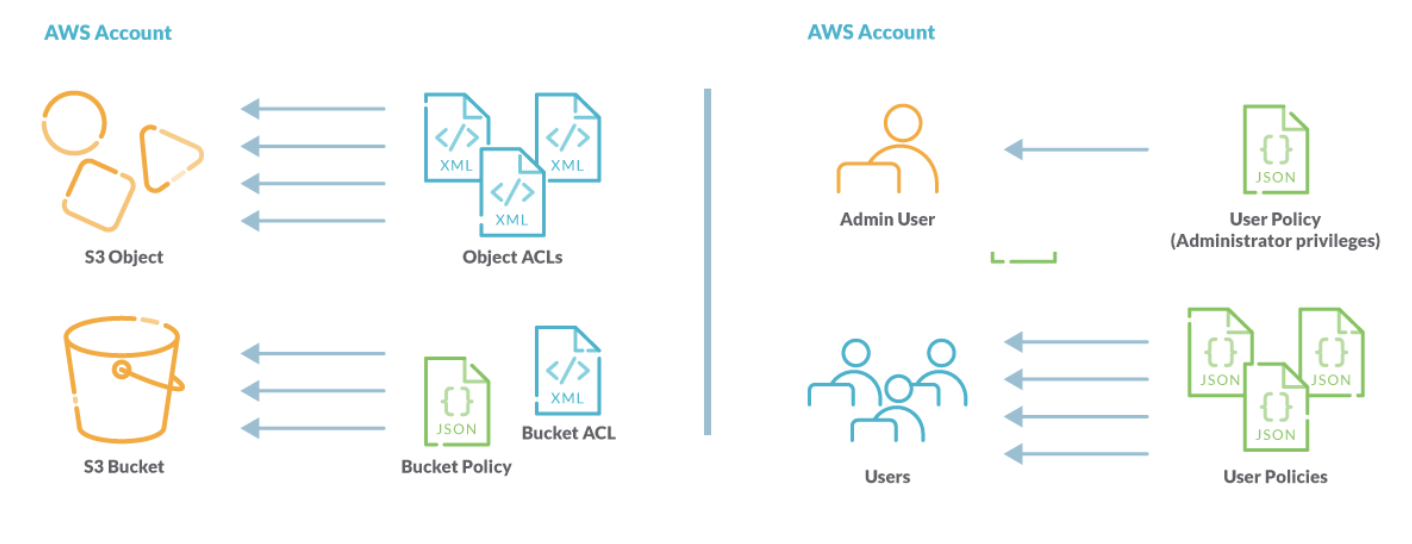
Everything about Identity & Access Management (IAM) in AWS Best Practices of Identity and Access Management (IAM) of Amazon Web Services (AWS) performs certain relative audits and removes all unused users and credentials. It is to secure the AWS resources for certain AWS Identities and Access Management Services (IAM). To Lock Away the AWS Account Root User Access Keys.

Aws best practices
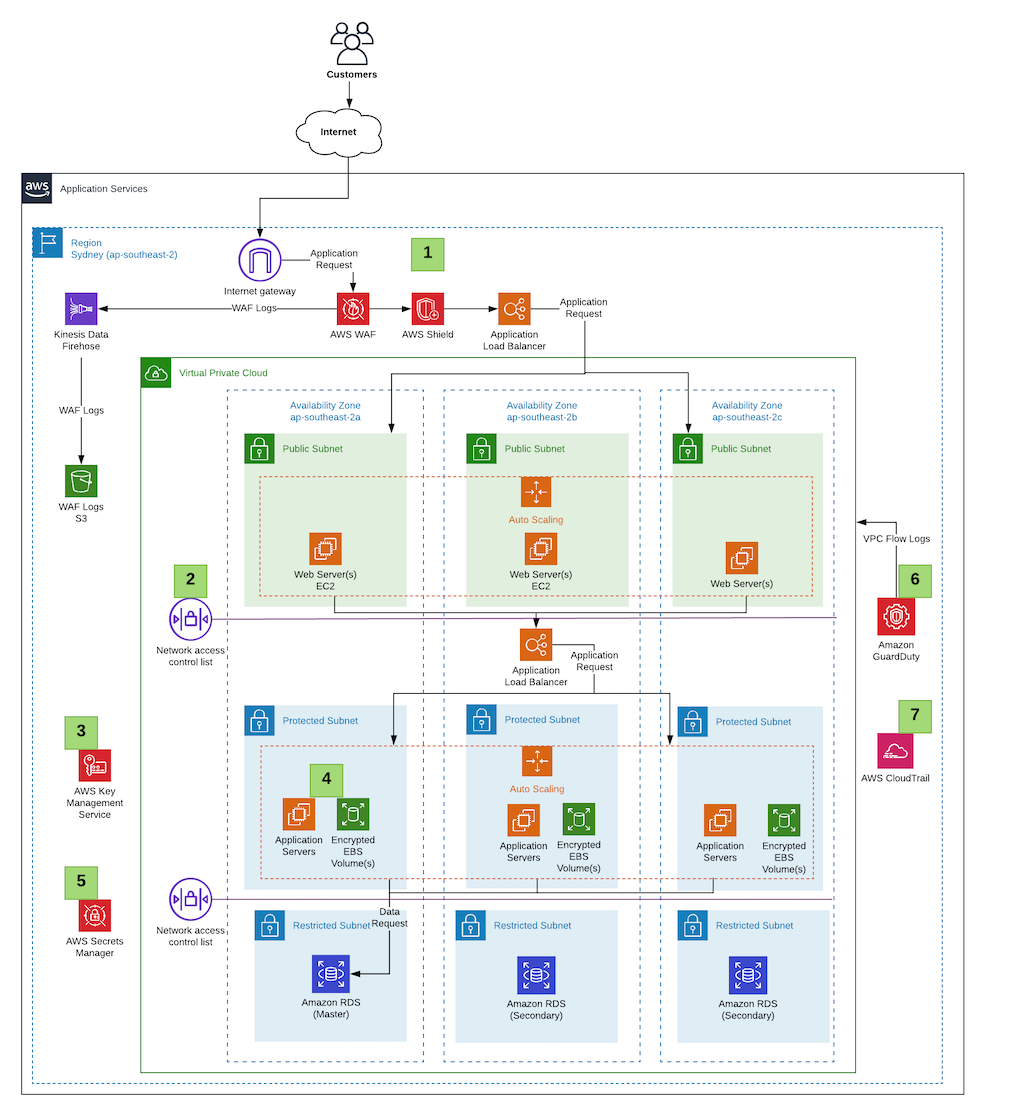
AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material. nOps' Best Practices Guide to AWS EDP | nOps AWS Knowledge Base Learn best practices for Cloud Security, Cost Optimization, Well-Architected Framework. Glossary of Terms Access the CloudOps Glossary for AWS and Azure. FAQ Get answers to frequently asked questions about nOps. nOps Developer Toolkit Access your cloud data at your fingertips. 10 AWS Architecture Best Practices - CLIMB The AWS Well-Architected Framework is a set of best practices for building secure, high-performing, resilient, and efficient infrastructure on AWS. It provides a way to measure your architecture against the best practices and identify areas where you can improve. The framework consists of five pillars: security, reliability, performance ...
Aws best practices. An introduction to AWS IAM best practices. Here are some best practices to enhance IAM effectiveness and help avoid common security mistakes. Never use root credentials. A business might create a single AWS account with root credentials ... 51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security. 10 AWS Architecture Best Practices - CLIMB The AWS Well-Architected Framework is a set of best practices for building secure, high-performing, resilient, and efficient infrastructure on AWS. It provides a way to measure your architecture against the best practices and identify areas where you can improve. The framework consists of five pillars: security, reliability, performance ... nOps' Best Practices Guide to AWS EDP | nOps AWS Knowledge Base Learn best practices for Cloud Security, Cost Optimization, Well-Architected Framework. Glossary of Terms Access the CloudOps Glossary for AWS and Azure. FAQ Get answers to frequently asked questions about nOps. nOps Developer Toolkit Access your cloud data at your fingertips.
AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material.







![AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT](https://blog2opstree.files.wordpress.com/2021/03/image-36.png)

















0 Response to "40 aws best practices"
Post a Comment